Secure Computing Compliance Overview
Currently, CARC systems do not support the use or storage of sensitive data. If your research work includes sensitive data, including but not limited to HIPAA-, FERPA-, or CUI-regulated data, please contact us at carc-support@usc.edu before using our systems. For more information on the different types of sensitive data, see the USC IT Services Data Security page.
Working with sensitive data that is governed by compliance regulations comes with additional requirements and restrictions that must be taken into consideration. The Center for Advanced Research Computing (CARC) plans to deploy a Secure Research Computing Environment (SRCE) in the future. SRCE is designed for researchers who need to meet various compliance standards required to use highly sensitive data. SRCE provides custom-sized servers (Windows, Linux, and/or containerized applications as a service) as well as secure data transfer methods for researchers.
SRCE is configured with the appropriate security controls and minimizes the risk of exposing high-risk data. SRCE makes it easier for researchers to implement necessary safeguards for research that is subject to regulatory or compliance requirements, including but not limited to, HIPAA, FERPA, CUI, and other grant-specific regulations.
Until SRCE is deployed, researchers managing sensitive data should refer to the following information on data sensitivity, data classification, and research data management.
0.0.1 What is research information?
Research information is defined as data that is developed as part of USC’s research programs and is protected under contractual agreements with public and private entities. Research information may have explicit restrictions on how data can be accessed, transported, and shared, and this data may be regulated under additional laws, such as EAR, ITAR, HIPAA, and the Food and Drug Administration (FDA).
Research information contains intellectual property that was developed either solely by USC, in conjunction with other research organizations, or subcontracted with public and private entities. The ownership of the intellectual property may be owned by USC, co-licensed with another organization, or owned by a third party.
0.0.2 USC data classification standards
USC classifies data into three primary categories in accordance with its data protection policies:
- Confidential Data typically includes regulated data requiring compliance efforts if exposed to unauthorized parties.
- Confidential-Controlled Data is a subcategory of Confidential and is to be used only for Covered Defense Information, which includes Controlled Technical Information (CTI), Controlled Unclassified Information (CUI), or any other data that has military or space application where the data provider (e.g., research sponsor) has imposed safeguarding or dissemination controls for reasons of national security.
- Internal Use Only Data includes all data used to conduct USC business, unless categorized as Confidential or Public.
- Public Data is not regulated and is generally made available through public interfaces and requires no protection mechanisms.
In order to quickly identify USC’s most sensitive data and the systems that create, use, store, transmit, and archive USC data, USC identifies data based on the type of data that it is (e.g., student data, research data, etc.) and assigns the appropriate classification level based on the level of importance the data holds to USC:
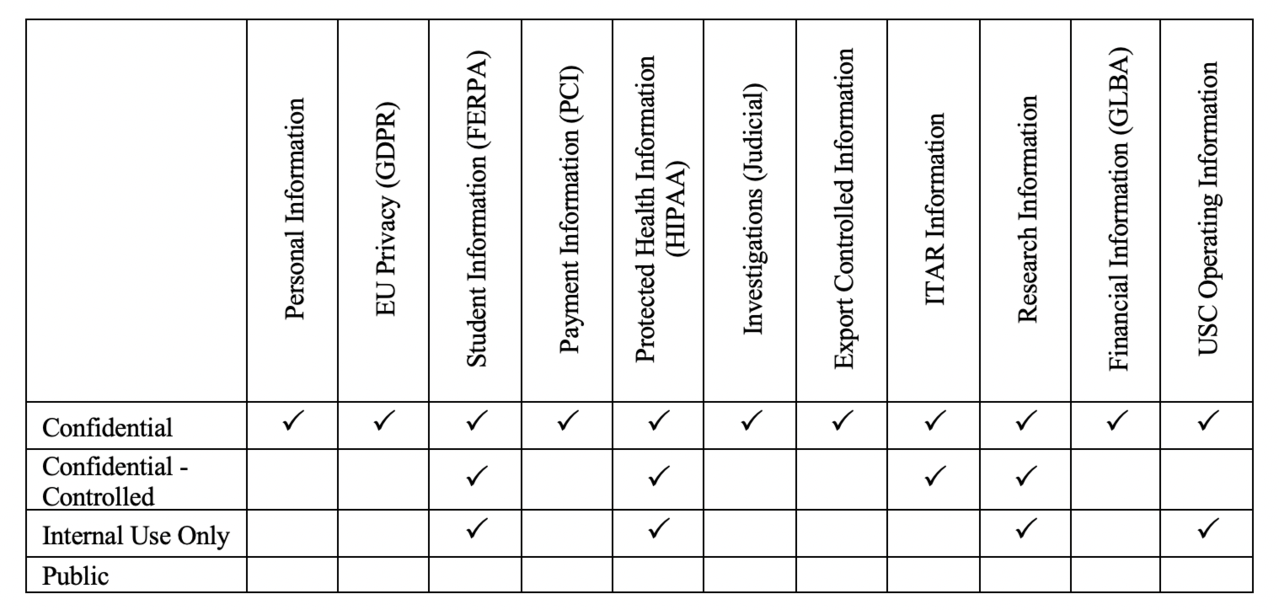
Most highly-sensitive research data falls under the Confidential-Controlled category. For example, research data under HIPAA and ITAR compliances are considered Confidential-Controlled. The confidentiality is the most critical aspect of the management of sensitive information, and the availability of the sensitive data should only be possible through a well-controlled environment with appropriate security measures.
USC’s Office of Culture, Ethics and Compliance has extensive documentation on data privacy for different types of sensitive data. More information can be found here.
0.0.3 CUI compliance
Controlled Unclassified Information (CUI) is federal non-classified information the U.S. Government creates or possesses, or that a non-federal entity (such as USC) receives, possesses, or creates for, or on behalf of, the U.S Government, that requires information security controls to safeguard or disseminate. These controls must be compliant with the federal regulations specified in 32 CFR Part 2002 and NIST SP 800-171.
0.0.4 HIPAA compliance
HIPAA (Health Insurance Portability and Accountability Act) information is defined as protected health information (PHI) that is created, stored, used, transmitted, or archived by a HIPAA-covered entity in relation to the provision of healthcare, payment for healthcare services, or use in healthcare operations. PHI contains details that may be used to identify an individual based on their past, present, or future health status, as set forth under HIPAA (45 CFR 164).
HIPAA research data is usually a “limited” data set, which is the PHI that excludes direct personal identifiers of the individual. It is still required to be used in a secure environment, and a review process is usually involved before granting access to the data, unlike de-identified data sets.
More information on HIPAA:
Health Information on the Office of Culture, Ethics and Compliance’s website
USC HIPAA Privacy Education Program
Definition of Limited Data Set (LDS)
0.0.5 FERPA compliance
FERPA (Family Educational Rights and Privacy Act) information is defined as data that is associated with an applicant, admitted candidate, or currently enrolled student of academic institutions. This data contains details about a student which includes personal, academic, and university administrative data that is defined and protected under FERPA.
The SRCE can only intake FERPA data under very special circumstances, as access to FERPA data even for academic research work requires written consent. If you plan to use FERPA data for your research, it is recommended that you consult the Office of Academic Records and Registrar and the Office of Culture, Ethics and Compliance.
More information on FERPA:
FERPA Information on the Office of Culture, Ethics and Compliance’s website
0.0.6 ITAR compliance
ITAR (International Traffic in Arms Regulations) information is defined as data that is protected under ITAR. ITAR information has explicit restrictions on how the data can be accessed, transported, and shared. This data is restricted under the controls set forth by the U.S. Munitions List (USML) code that is assigned to USC data and assets by the Directorate of Defense Controls (DDTC) and defines the restrictions on who can access the data and where the data can be accessed from or transported.
Researchers conducting defense-related projects funded by DOD, DOE, ARMY, AFOSR, or ONR may encounter data with Export-Controlled or ITAR compliance. These compliances require restricted control over data management as well as security around the physical systems. CARC’s Secure Research Computing Environment is not capable of handling this type of compliance, but special arrangements can be made depending on a project’s requirements. Please contact carc-support@usc.edu if your research work uses ITAR information.
More information on ITAR:
ITAR Information on the Office of Culture, Ethics and Compliance’s website